Enable DNS over HTTPS and Encrypted SNI in Firefox
In Firefox 62, Mozilla has added two new features called DNS over HTTPS (DoH) and Trusted Recursive Resolver (TRR). The ideal behind each of these features is to improve user privacy and improved performance. DNS has typically been sent over insecure HTTP allowing anyone on the wire, such as your ISP, to monitor what sites you are visiting.
Below we’ll look at how to enable TRR you can tell Firefox to make DoH it’s first choice and use the system DNS as a fallback option.
The second feature we will be enable is Encrypted SNI, which prevents others from intercepting the TLS SNI extension and use it to determine what websites you are browsing.
How to enable Trusted Recursive Resolver and ESNI in Firefox
- First download and install the latest version of Firefox browser.
- In the Firefox address bar type in the about:config and click on “I accept the risk!“
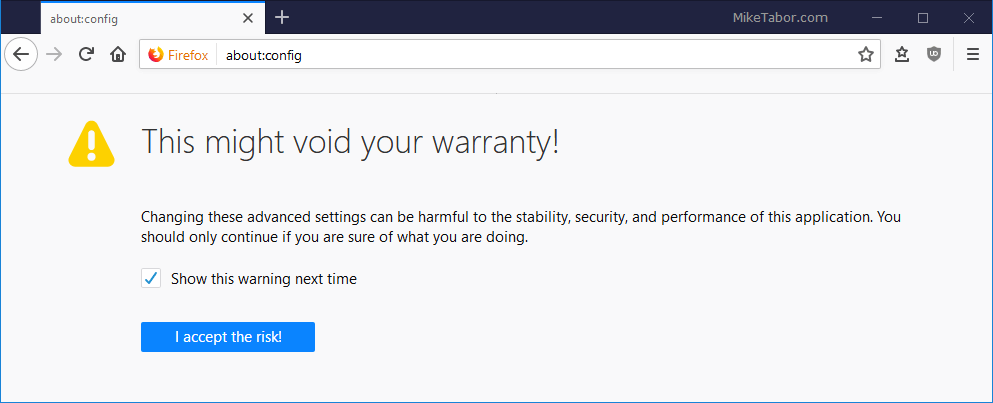
- Next search for network.trr.mode and change it’s value from 0 to 2.
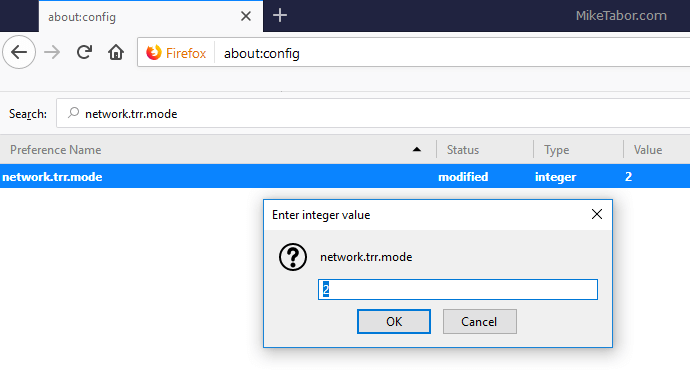
- Now, in the search box type in network.security.esni.enabled. It’s default value will be set to “false”, double click on it to change the value to “true”.
Further, you can check your browsing experience security by heading over to https://www.cloudflare.com/ssl/encrypted-sni/
Alternative DoH endpoints
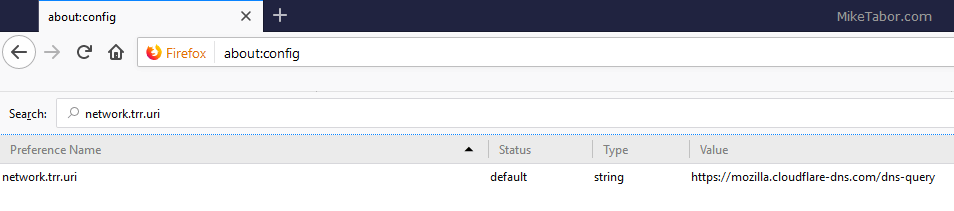
By default, when you enable DNS-over-HTTPS your requests will go through Cloudflare at: https://mozilla.cloudflare-dns.com/dns-query
However you can use any DoH compliant endpoint by changing the network.trr.uri value to any end point that supports it, such as:
- Google DNS: https://dns.google.com/experimental
- Quad9: https://dns.quad9.net/dns-query
How to disable Trusted Recursive Resolver
Not everyone is overly excited about the new TRR feature, since all of your DNS traffic would be sent to Cloudflare.
If that is the case for you, you can easily turn off TRR for good by setting network.trr.mode to 5.
Here are the current network.trr.mode values:
- 0: Off by default
- 1: Firefox will choose based on which is faster
- 2: TRR preferred, fall back to DNS on failure
- 3: TRR only, no DNS fallback
- 5: TRR completely disabled
Which do you trust more, your ISP or Cloudflare? Do you have TRR enabled or have you set it to 5 to ensure it stays disabled? Let me know below!
There’s an important missing point here. In order to use mode 3 (enforced), the setting “trr.bootstrapAddress” must be set to a trusted DNS resolver which will be used to resolve the domain in the “trr.uri” setting.
If “trr.bootstrapAddress” is left empty (as it is by default), DoH will not work in mode 3.
I followed the steps to switch on DNS over HTTPS using Cloudflare in Firefox 66.0.1 , but the first two test fields: Secure DNS and DNSSEC do not pass – “You may not be using secure DNS.” and “Your resolver does not appear to validate DNS responses with DNSSEC.” The last two tests pass – “Your browser supports TLS 1.3, which encrypts the server certificate.” and “Your browser encrypted the SNI when visiting this page.”
Please let me know why this is.
I got that too, caused by NoScript Firefox-addon. You are using NoScript or maybe uBlock Origin?
You must change DNS ip address in your network card TCP/IPv4 settings. Control panel > network connections > right click on active connection > properties > TCP/IPv4 > set DNS servers to 1.1.1.1 (cloudflare) and 8.8.8.8 (google).
Set it to 5, thanks for the info. Don’t like this feature at all – how is it good for privacy/security to send all DNS queries to Cloudflare?
Can’t be any worse than leaving all DNS quaries in plain text for my ISP to read and then probably sell the info. My ISP is Xfinity, I will take my chances with Cloudflare.
You could also use PiHole to do all this if a home network.
That way all devices, even if they do t support it will be direct via the PiHole proxy to DoH
ESNI is a browser feature only though I believe
eSNI makes it possible to even hide the queried server, in particular, the service during the TLS handshake/ClientHello. Although, the public keys for eSNI are distributed via DNS. So, does not it result in a loop if I use DNS over HTTP or TLS?
And doesn’t it mean that I will never be able to hide from the ISP that I am using a specific encrypted DNS resolver? In other words, the main reason is privacy and not letting be censored. However, if ISPs can identify from SNIs which DoH services I am using, they can block those services. (I only said DoH in the end, because DoT uses a well-defined port number that can be filtered if needed, however, DoH relies on HTTPS 443 port that cannot be filtered of course).
FF passed the tests, but Iridium and new Chromium Edge did not on the “Encrypted SNI”. Is there a way to secure that on those browsers? Thanks for any help on this.
PS…I’m using “DNS Jumper” little program. Is that trustworthy? Thanks again.
This is weird…
I tried getting the sni encrypted in waterfox. It did not work. Some minutes later without me touching anything the test passed it, showing up it works.
However I tried again today the test and does not show up the sni as encrypted. I open up firefox try the text on waterfox again and it passes the test.
However firefox does not pass the test never…
But I did all instructions everything is as it should be for firefox passing the test…
Oh wait. Now firefox passes the test.
Just one question I need to know… do I need to use cloudfare dns for the sni to work properly?
Because right now I am using both ibm and cloudfare dns…