VMware releases patch for glibc vulnerability on ESXi 5.5
You may remember not to long ago, the GHOST vulnerability found in glibc, a GNU C library. Well a new glibc vulnerability (CVE-2015-7547) has been discovered and it affects VMware ESXi 5.5 and 6.0 in addition to all versions of VMware virtual appliances running Linux such as vCenter, Orchestrator, vRealize, etc.
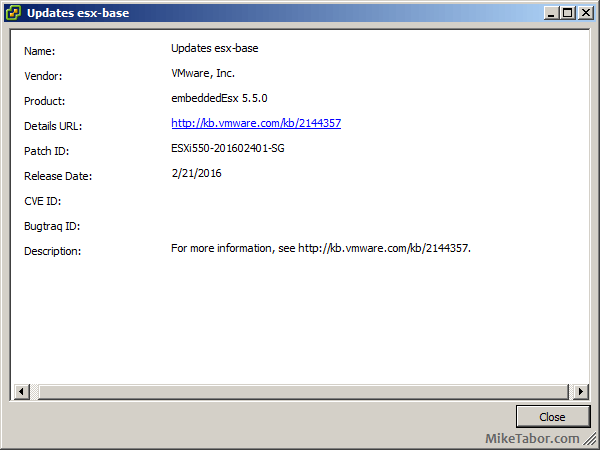
VMware has just released patch ESXi550-201602401-SG for ESXi 5.5 and ESXi600-201602401-SG for ESXi 6.0 which fixes the glibc vulnerability, a patch for ESXi 6.0 has yet to be released. VMware has however posted workarounds for affected virtual appliances.
In addition, ESXi550-201602401-SG also fixes two other issues:
- ESXi hosts might purple screen due to an unresponsive CPU as a result of several CMCIs within a short time. Sample purple diagnostic screen might look like the following:
cpu1:33127)MCE: 1118: cpu1: MCA error detected via CMCI (Gbl status=0x0): Restart IP: invalid, Error IP: invalid, MCE in progress: no.cpu1:33127)MCE: 231: cpu1: bank9: MCA recoverable error (CE): "Memory Controller Scrubbing Error on Channel 0."cpu1:33127)MCE: 222: cpu1: bank9: status=0xXXXXXXXXXXXXXXXX: (VAL=1, OVFLW=0, UC=0, EN=0, PCC=0, S=0, AR=0), ECC=no, Addr:0xXXXXXXXXXXXXXXXX (valid), Misc:0x8c3589300 (valid) - Resolves the issue where virtual machine vMotions would fail when trying to vMotion from an ESXi 5.0 or 5.1 host to an ESXi 5.5 U3b host.
UPDATE: VMware has released ESXi 6 patch ESXi600-201602401-SG which updates the glibc package and patches the glibc vulnerability.
A host reboot will be required to apply the ESXi patches. After applying the patch your ESXi 5.5 host should have a build number of 3568722.